Workday Security: Everything You Need to Know
If you’re a malicious actor in cyberspace, you could do much worse than targeting a Workday instance at a large corporation. As one of the world’s leading Human Capital Management (HCM) applications, Workday holds valuable data from employees and businesses worldwide.
The scale of Workday’s user base hints at the level of risk: 50 million users in over 170 countries. Over a million users access Workday every hour, executing 365 billion transactions annually. The platform’s scale and inherent risks prompt a strict security approach.
Workday has rigorous security controls protecting its infrastructure. However, the problem is that much of the risk exposure inherent in Workday exists outside of what the company provides.
What is Workday Security?
Workday security is a series of security steps, protocols, and information security controls to mitigate risks in the complex Workday environment. Workday runs in highly secure data centers with network and infrastructure security operations. The company enforces strict application security (AppSec) policies, and all data is encrypted and subject to segregation by the client to protect the multi-tenant architecture.
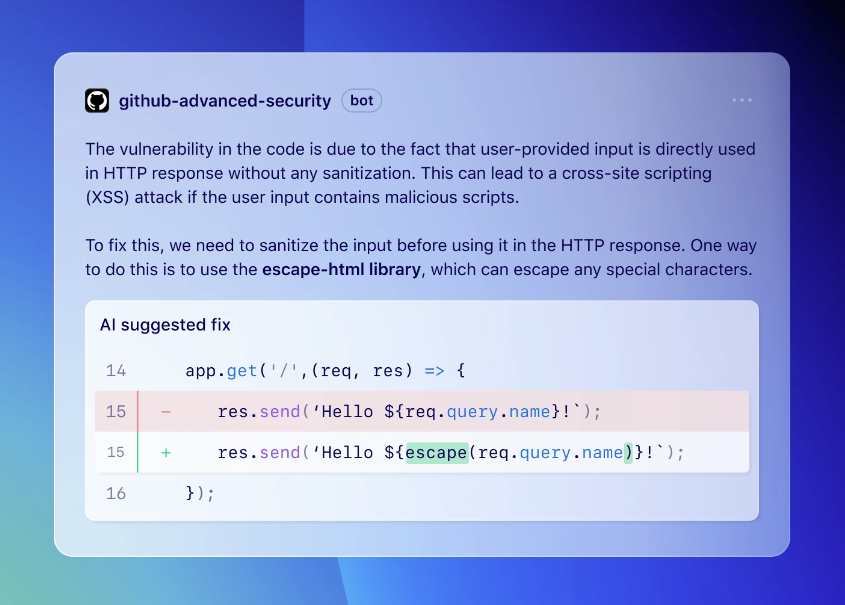
Passwords are “native login,” always hashed—never stored or transmitted in their actual forms. However, it’s worth paying attention to the type of password hashing algorithm used, as older methods may be inefficient. Modern algorithms like bcrypt or Argon2 are adaptive and more resistant to attacks, making passwords significantly more difficult and time-consuming to track. A modern, customizable hashing method is crucial to protect your Workday passwords.
But Workday offers other crucial security features. The whole application is subject to a single security model, so all user interactions are subject to the same policies and enforcement mechanisms. The platform also offers single-sign-on (SSO) using security assertion markup language (SAML) and multi-factor authentication (MFA).
Consider what’s going on inside a typical Workday instance. You might have salary and benefit information for thousands of employees worldwide. Employees can see their salary and benefits, not anyone else’s. Administrative users may have greater visibility into this private information and be able to define access controls and security configurations.
This power ensures that no one sees what they’re not supposed to see and that no outsider can view, exfiltrate, modify, or delete any data. Still, Workday is a SaaS app like any other, so it suffers from the same SaaS security challenges. Just like you would secure your Salesforce environment to protect customer data, you should apply extra security measures to your Workday platform to protect employees’ private information.
Why Should You Care About Securing Your Workday Platform?
Workday’s extensive user base and dynamic functionality make it vulnerable to cyber threats. At most Workday companies, virtually every employee can access the software, subject to a broad and often complex range of permissions. The software integrates with other systems, too, which further expands the attack surface.
Despite having its robust security features, Workday still faces various risks. Most of these risks stem from using and integrating this SaaS app with other apps, but they can be mitigated with the proper SaaS security best practices. As a Workday client, here are the common security threats you should be concerned about:
- Phishing attacks—Malicious actors can trick employees into sharing their Workday login credentials or other information that lets them gain unauthorized access to the application.
- Credential stuffing attacks—If attackers have stolen passwords, such as those on the dark web, they can try to access Workday by pairing known user emails with possible passwords. This attack can work if MFA is not switched on and users use the same password for personal accounts.
- Insider threats—Employees may abuse their access to the application for many reasons, ranging from curiosity to disgruntlement and greed. Privileged users comprise the most severe insider threat.
- API threats/integrations—Workday connects with many popular enterprise applications through its application programming interface (API). The same API can be the basis for integration with virtually any software. Depending on how you configure the API, it may be vulnerable to threats like broken access control or injection attacks. Left un-remediated, vulnerable APIs can leak data to unauthorized parties.
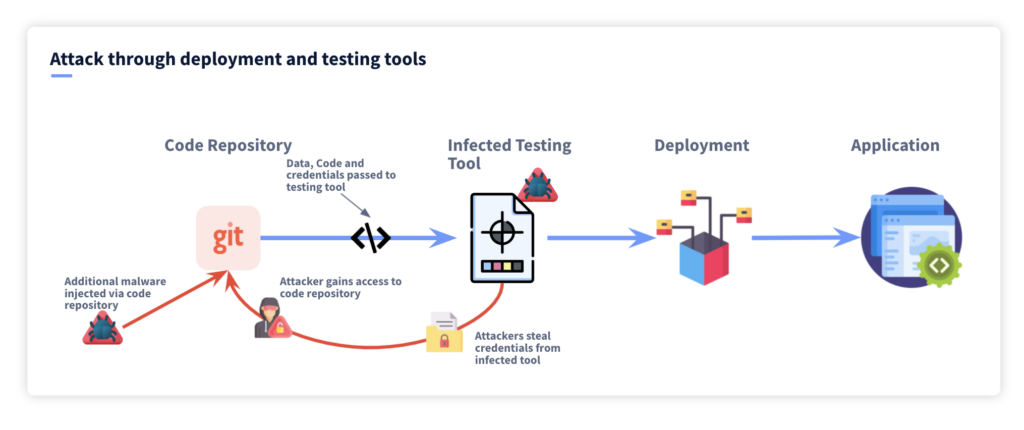
- Supply chain attacks—Workday offers an integrated development environment (IDE) so developers can build custom add-ons and integrations for the software. By allowing custom code from outsiders, Workday could enable insecure software development processes. This exposes Workday customers to supply chain attacks like malicious code injections, social engineering, and compromised dependencies.
Challenges in Maintaining Workday security
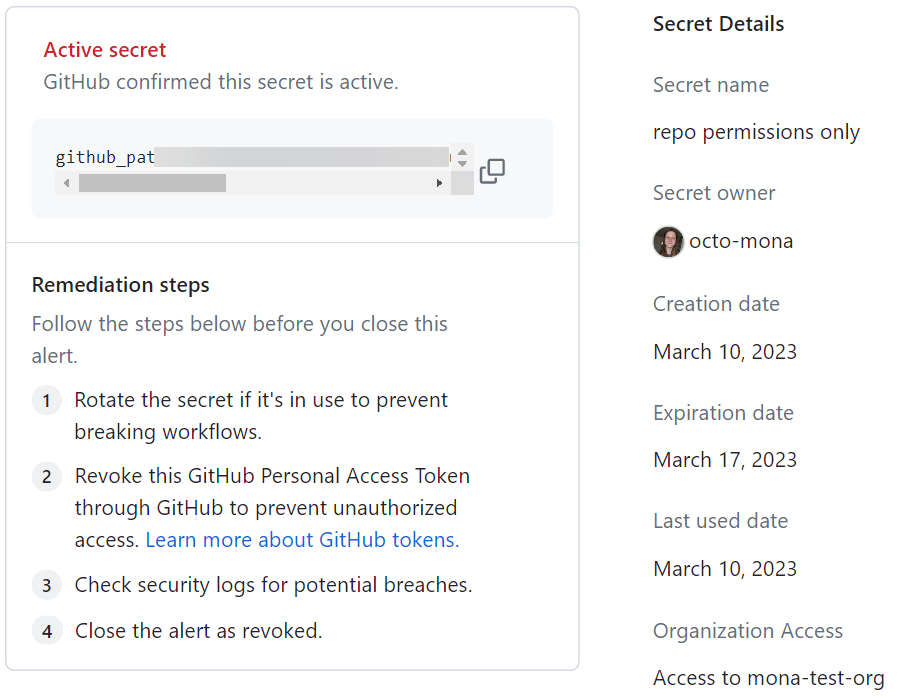
1. Overprivileged accounts
It is possible to let some Workday accounts become overprivileged, even if accidentally. For example, if a user has an admin role but then switches to a new job that does not require admin access and that access is not revoked, the user has excessive privileges. Bad actors can exploit these to access and steal sensitive data, manipulate settings, or approve financial transactions.
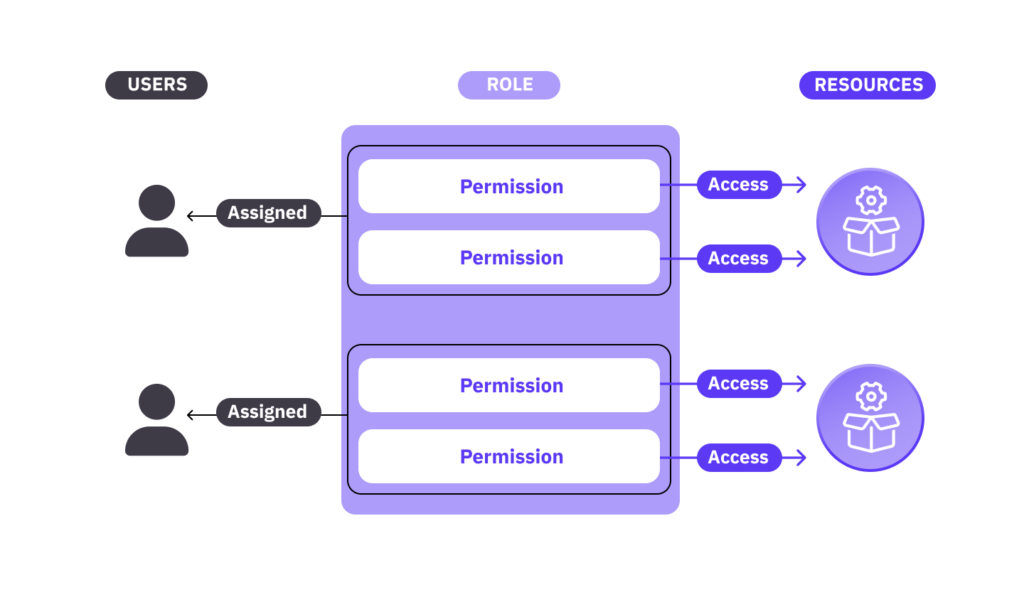
2. Complexity of roles, hierarchies, and organizational structures
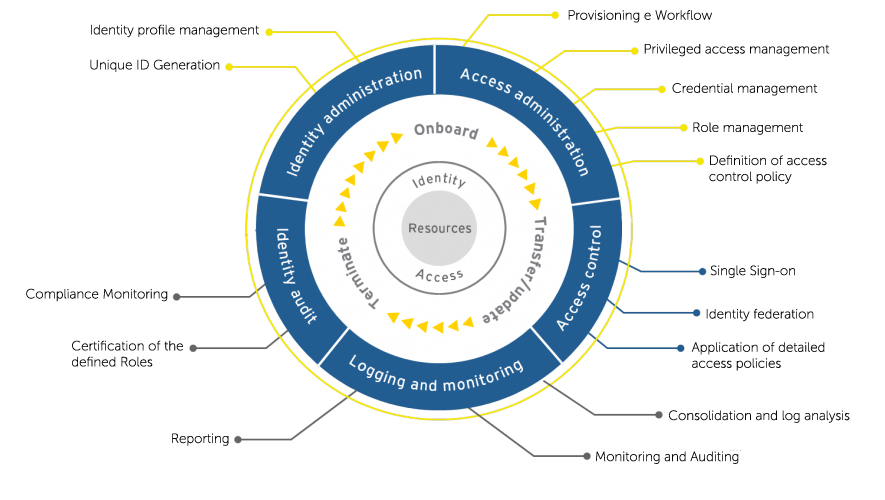
Workday allows you to create highly complex user roles with access rights that map to organizational structures and hierarchies. This level of detail is excellent because you can set up your access how you want it. However, organizations are dynamic, and over time, the role definitions you set up will become obsolete, creating risk exposure in the process.
3. Lack of visibility over access controls
The complexity of roles and their respective privilege leads to a situation where security admins may lack visibility into access controls. Workday does provide an interface with a view of access controls, but when there are thousands of users to manage, with varying and ever-changing permission levels, admins struggle to parse who can do what on the software.
6 Steps to Improve Workday Security
1. Monitor security configurations
Security admins’ flexibility and discretion can lead to insecure configurations, such as overly permissive bring-your-own-device (BYOD) policies or a lack of MFA. These misconfigurations allow attackers to enter your systems and can be very challenging to spot. To monitor security configurations properly, you should use an automated monitoring tool like Suridata, which scans configurations continuously and flags problematic ones.
2. Create a privileges inventory and regularly update it
Keep your Workday access model simple and map it clearly to your organizational model and role definitions. The result will be an inventory of privileges that identifies what every type of user can see and do on Workday. This inventory should include the privileges granted to Workday integration system users (ISUs) and Integration Security Groups (ISSGs). Keeping this inventory up to date has to be someone’s job, and executive sponsorship may be necessary to ensure the budget to cover this cost.
3. Deploy API security and third-party security countermeasures
The Workday API is a potential attack surface, so deploying countermeasures that mitigate API risk is a best practice. Firstly, it’s worth familiarizing yourself with the top 10 risks for OWASP API security. This list gives you a comprehensive overview of the threats to look out for and how attackers exploit these gaps. Then, using a dedicated API security solution, you can scan your environment for “rogue” APIs that may have been abandoned but expose Workday data to external API clients. These tools can also monitor API security settings and flag insecure APIs.
4. Employ Secure DevOps practices
If your organization uses the Workday IDE and leverages DevOps, you should employ AppSec methods in your development process. One key component of AppSec is code scanning, for which you can employ SAST and DAST tools to identify vulnerabilities early. Integrating “shift left” security remediation can also help you embed the proper security controls during development, preventing you from having to fix vulnerabilities while your Workday app is running.
5. Continuous compliance monitoring
The personnel data on Workday is subject to several laws regarding consumer privacy, depending on where you operate. If you have employees in California, you must comply with CCPA, for example. If you’re in Europe, it’s GDPR. Violations of these laws can be costly and time-consuming to remediate.
You can reduce your compliance risk by continuously monitoring for compliance (for instance, checking that data is in the correct sovereignty and no data about German citizens is stored in France).
6. Continuously scan for insecure data
Workday is likely just one element in your broader SaaS ecosystem. It’s also likely to be connected to other SaaS apps you use, such as online storage solutions. One risk in these conditions is that users will move data from Workday to another app, such as an online storage platform. This data storage can be highly insecure, leading to the risk of breach, exfiltration, and all the expensive remediation actions that follow such an event.
SaaS security solutions like Suridata can continuously scan for personnel data across the entire SaaS ecosystem, automatically flagging data that needs to be removed and providing detailed insights into the issue so you can activate the proper remediation workflow.
Making Workday SaaS Secure
Workday has many security features, but the software remains vulnerable to threats like phishing attacks, API attacks, and brute force. Complex access rules compound the problem. To make Workday more secure, you must implement countermeasures addressing these risks.
Suridata can make securing your Workday platform and data much more manageable. The Suridata tool scans your entire SaaS ecosystem (Workday and beyond, no matter how many SaaS apps you have), monitoring Workday’s security configurations, spotting any abnormal user behavior, and accurately identifying data that might have been mistakenly or maliciously exported from Workday. Interested in seeing it in action? Schedule a demo with our team.
Co-Founder & CPO