Dropbox Sign Security Breach
Overview of The Breach
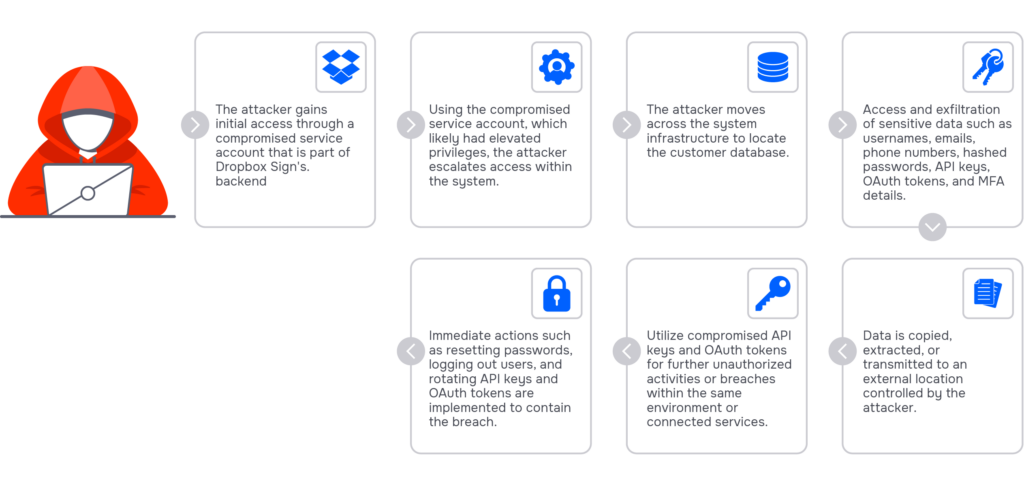
On May 2, 2024, Dropbox disclosed a significant breach involving its digital signature service, Dropbox Sign (formerly HelloSign). The breach was discovered on April 24, with unauthorized access traced back to a compromised service account within Dropbox Sign’s backend infrastructure. This allowed attackers to exploit elevated privileges and access a customer database, affecting all Dropbox Sign users.
Details of Compromised Data
The breach led to the exposure of sensitive information, including emails, usernames, general account settings, and for some users, phone numbers, hashed passwords, and critical authentication data like API keys, OAuth tokens, and multi-factor authentication (MFA) details. Notably, the breach also affected individuals who interacted with Dropbox Sign documents but did not create an account. This caused the exposure of their names and email addresses.
Potential Impacts and Dropbox’s Response
Dropbox has initiated several remedial actions in response to the breach. These include resetting user passwords, logging out users from connected devices, and rotating all compromised API keys and OAuth tokens. The company is currently reaching out to all affected users with specific guidance to secure their information. Dropbox is also cooperating with law enforcement and regulatory authorities.
The ultimate impact of this breach is unknown, but it is likely to be significant. Now that the attackers have critical authentication data, they can hop between customers’ accounts, retrieve more data, and put more customers in danger.
The Role of Suridata in Enhancing Security
The Dropbox Sign breach highlights the essential role of Suridata in both preventing and responding to similar cybersecurity incidents. With its capabilities in managing and securing third-party apps and APIs, Suridata is particularly valuable, especially as it integrates Dropbox as a core business SaaS application within its management framework. As the breach occurred in Dropbox Sign, which is an integral part of Dropbox’s suite of services, leveraging Suridata enables organizations to gain precise insights into their Dropbox account activities. This includes detailed tracking of account movements, connected plugins, and both human and non-human account interactions, along with the specific times each element was accessed. Moreover, Suridata provides a comprehensive risk analysis, identifying misconfigurations that could lead to unauthorized access.
Additionally, Dropbox serves as a third-party application used in various business applications. Suridata can identify on what applications Dropbox is being authorized, and point out where it should be isolated or where credentials should rotate.
For example, Suridata can assist with:
- Isolating sensitive integrations: Detecting and managing which third-party applications, like Dropbox Sign, are authorized to integrate with core business applications, recommending isolation or restricted access where necessary.
- Rotating and managing credentials: Identifying and implementing automated workflows for credential rotation for services connected to Dropbox Sign to prevent unauthorized access from compromised credentials.
- Enhanced view of account activities: Ensuring that all users and API activities within Dropbox Sign are monitored with alerts for any unauthorized access attempts or anomalous behaviors.
- Applying access controls: For example, enforcing policies that require multi-factor authentication for all accesses to Dropbox Sign.
- Regular risk assessment: Regularly scanning and assessing Dropbox Sign configurations and usage to identify potential security misconfigurations or vulnerabilities that could lead to breaches.
This proactive and detailed approach empowers organizations to enhance their security postures effectively, ensuring that their data remains secure while protecting sensitive data, against evolving cyber threats and maintaining trust with users.
Potential Attack Path
Product Lead
