A Guide to Role-Based Access Control in SaaS Applications
John logged into your company’s SaaS-based accounting app late last night and downloaded your customer list. There’s just one problem: John moved from Accounting to Marketing six months ago. But because you provisioned John’s SaaS access one app at a time, no one thought to change his permissions when he moved departments. This SaaS security risk is more common and dangerous than you might think.
26% of companies that reported a SaaS security incident were attacked by an insider. The picture looks even more threatening when you factor in additional security challenges like SaaS sprawl and shadow IT. Role-Based Access Control (RBAC) is one solution that will bring greater access and privilege management control in the SaaS environment.
Understanding Role-Based Access Control (RBAC)
Role-based access Control (RBAC) provides access to networks and systems based on a user’s role rather than their identity. Without RBAC, system admins must provide access and privilege levels for one user at a time.
Imagine manually assigning access permissions for every tool to each employee in your company. This process would be painfully time-consuming and error-prone, significantly hindering your SaaS security efforts. Under RBAC, admins could set access controls so only users with a specific role can access a particular system.
Aside from RBAC, there are three other access control methods: Mandatory Access Control (MAC), which leverages centralized access policies; Discretionary Access Control (DAC), which gives any resource owner the flexibility to grant permissions; and Attribute-Based Access Control (ABAC), which makes access decisions based on attributes like location and time.
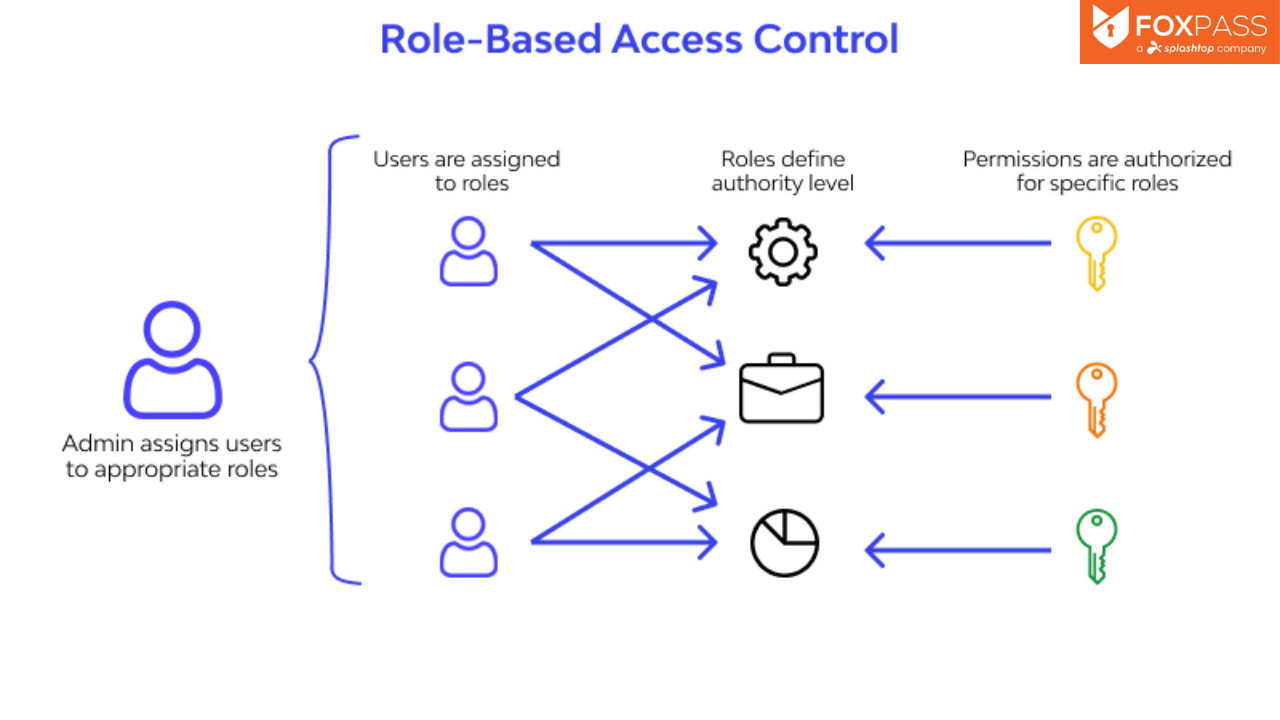
The Critical Components of Role-Based Access Control (RBAC)
RBAC operates through three key components: roles, permissions, and users. Roles typically align with an organization’s structure, often based on departments or hierarchy. For example, in Salesforce security, an “Executive” role might be able to view all sales reps’ deals, while a “Sales Rep” role would limit access to only the deals of the individual rep.
This example illustrates how roles are tied to specific permissions. For instance, an “Admin” role may grant access to a system’s administrative back end, while a “Super Admin” role offers even deeper access. This structure is known as a “role hierarchy.”
Role-Based Access Control in SaaS Security: What are the Benefits?
- Higher efficiency—With RBAC, admins can more efficiently provision access and privileges at a granular level. For example, it’s faster and simpler to grant everyone with the “Sales Rep/California” role access to accounts in California versus assigning that access to each sales rep in California individually.
- Enhanced SaaS security—With RBAC, it is less likely for a user to have excessive privileges, reducing the risk of unauthorized SaaS application access and data breaches
- Simplified Identity and Access Management (IAM)—RBAC streamlines granting or revoking user access as employees join the company and change roles.
- Scalability—By grouping access rights and privileges by role, RBAC makes it easier to scale and apply access control to your organization’s growing portfolio of SaaS apps.
- Improved compliance—Some regulations and industry compliance frameworks require reporting and audits on user access rights. RBAC makes these processes more manageable.
RBAC in SaaS Security: Challenges and Solutions
RBAC can be challenging to implement in SaaS security. For starters, most SaaS apps already have their own built-in RBAC settings. For instance, the Salesforce Security Model enables users to define roles, profiles, and permission sets.
While that’s beneficial, you can’t custom-configure roles in dozens of SaaS apps. You must also align access changes with IAM systems and protocols, ensuring you follow your organizational security procedures. On top of that, your customization levels depend on the vendor’s features and differ from app to app.
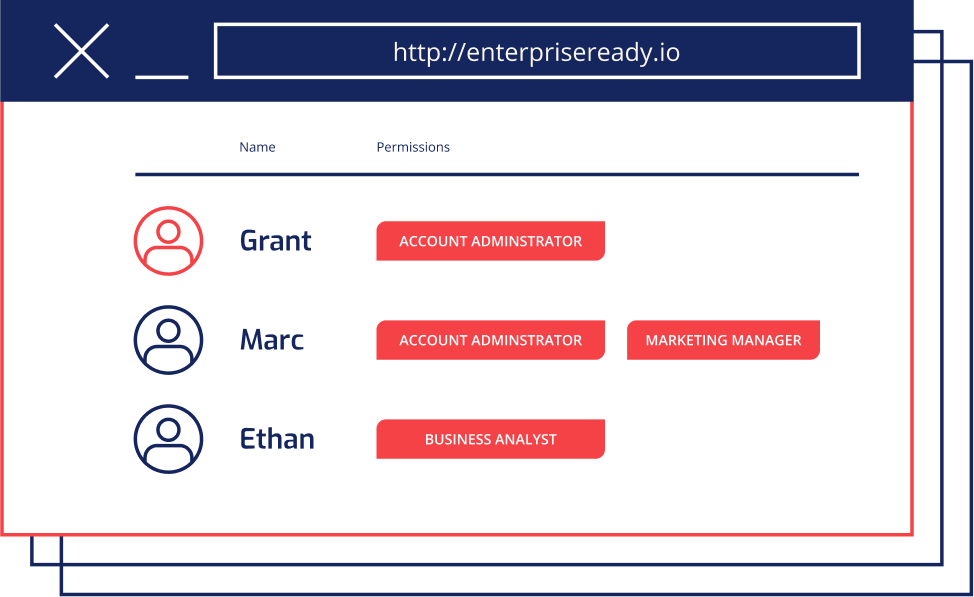
For example, if you assign Ethan the “Business Analyst” role in Salesforce, they will not be a “Business Analyst” in any other SaaS apps. Access needs change over time, so realistically, you’ll never keep up with it on an app-by-app basis. Additionally, you will have difficulty monitoring RBAC if you have separate role settings on each of your SaaS apps.
How to Implement Role-Based Access Control in SaaS Applications
To make RBAC work as a factor in driving better outcomes for SaaS security, you need a solution that deploys RBAC across multiple SaaS apps. SaaS security solutions like Suridata facilitate this functionality. They integrate with IAM, enabling you to restrict access across the whole SaaS environment. This also means a change in role access rights in the central IAM/SaaS security solution applies to every SaaS app. This process sounds simple, but there are a few other steps required to implement RBAC in SaaS:
1. Identifying Roles and Permissions
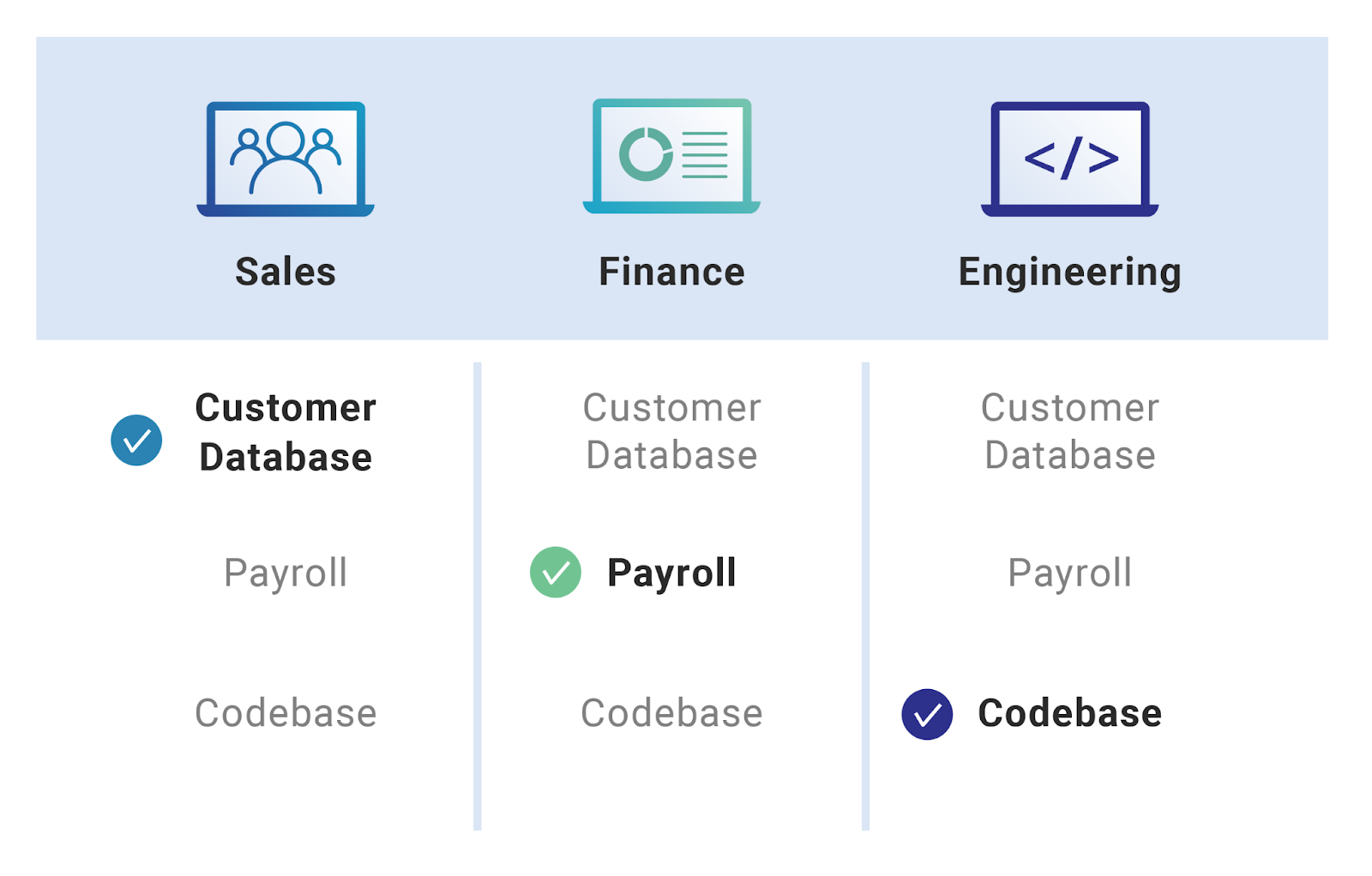
Before you integrate IAM with SaaS for RBAC, it is essential to think through how your RBAC policies will apply to SaaS. You have a head start if you already have RBAC for your on-premises applications. However, you must still figure out who is who and who needs access to what data and SaaS functionality.
The “who can do what” chart will inevitably relate to organizational structures and compliance requirements. For instance, regulations may require the company to audit and report on access privileges for people in the finance department, so the IAM-RBAC mapping for SaaS must consider this.
Implementing IAM-RBAC for dozens of SaaS apps simultaneously is not practical. Hence, a prioritized “heat map” that organizes SaaS apps based on their risk levels and criticality can help you know where to start. You can also download a risk assessment template for SaaS to ensure you review your apps across every essential factor.
2. Reviewing Your Vendors’ RBAC Capabilities
Third parties are aware of the vendor-related risks they may bring to your organization, so they often provide crucial security tools to help you protect your systems from external threats. It may turn out that your highest-priority SaaS apps already have the RBAC capabilities you need built-in.
These capabilities can give you extra time while you plan a more complete IAM-RBAC-SaaS integration. You may need to customize the app’s RBAC settings to fit your needs, but you’ll still avoid the full complexity of integrating IAM with SaaS. However, it’s essential to continuously monitor the built-in RBAC features to catch any potential issues with user access.
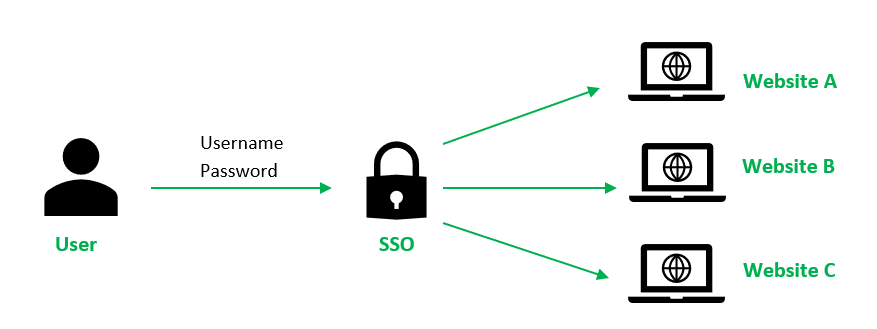
3. Implementing Single Sign-on (SSO) Integration
By setting up SSO, your users only have to log in once and can then access all IAM-RBAC integrated SaaS apps per RBAC policy. This setup helps with productivity and user experience.
4. Integrating with External SaaS Security PM and IAM Solutions
To implement RBAC across multiple SaaS apps, you must integrate your IAM solution with each of your SaaS apps. These integrations will require custom work, such as coding, to integrate with the various APIs. Plus, you may want to integrate your SaaS security solution, too. The SaaS security solution can monitor user activity and flag problems like inconsistent use of MFA or suspicious signs-in on “local” accounts.
5. Configuring User Provisioning and Deprovisioning Workflows
Each time a user needs access to a SaaS app under RBAC, you must provision that access based on RBAC rules. The same goes for deprovisioning. The challenge here is to set up a streamlined workflow that does not require too much administrative attention. You don’t want a situation where an admin has to provision or de-provision role-based access manually. Ideally, roles are assigned upon hiring—and then automatically flow to access provisioning. Similarly, you should automate role changes.
6. Leveraging an Identity Posture Management (IPM) Tool
Getting these moving parts to work together is only part of the challenge of making RBAC work for SaaS security. You will ideally have a SaaS security solution that continuously monitors and reviews user sessions and account configurations.
With Identity Posture Management (IPM), you get the efficiency and security benefits of RBAC in SaaS while maintaining your overall identity posture. This method lets you promptly detect and remediate insecure access situations before they lead to data breaches.
Getting Granular and Efficient Access Controls
Granular access controls are crucial to tighten access to sensitive data and functionality, and RBAC is the most efficient way to implement them. By assigning access based on a role, you avoid the tedious and error-prone practice of provisioning and deprovisioning access on a user-by-user and app-by-app basis.
Of course, RBAC still doesn’t make access management the most straightforward process ever. SaaS apps often have their own RBAC controls, which may not align with your preferred approach to access privileges. Plus, you may have to integrate your IAM solution with each SaaS app so that a role defined centrally can be applied to all connected apps.
If you want to simplify RBAC and ensure that every system layer is protected, Suridata can help. As a SaaS Security platform, Suridata can identify all your SaaS integrations and usages to detect access control gaps and other vulnerabilities, providing instant alerts and enriched insights. Learn more here.
Co-Founder & CPO
