How to Correctly Perform the 5-Step Security Risk Assessment
Did your mother ever tell you not to open the door to strangers? She knew best: there was a chance, however small, that something bad would happen. She’d done her version of a security risk assessment (SRA) to protect you from harm. Cybersecurity may be a lot more complex, but the risk management concepts aren’t all that different.
Nearly three in four organizations have experienced one or more significant disruptions due to third parties in the last three years. Your enterprise has likely opened its doors to vendors and partners so you can continue to improve your products and customer service. However, a chain is only as strong as its weakest link, and failing to assess third-party risks can weaken your security posture. An SRA is a valuable step in protecting your digital assets—and in some cases, it may even be legally required.
What is a Security Risk Assessment?
A Security Risk Assessment is a structured review and analysis of cybersecurity risks. While the implementation process may vary, it always involves identifying risks, estimating their likelihood and impact, and prioritizing mitigation through controls and countermeasures. The details may be complex, but the goal is simple: pinpoint the most damaging cyber risks and focus on minimizing their chances of occurring.
The SRA should interest various stakeholders:
- Chief Information Security Officer (CISO)
- Chief Information Officer (CIO)
- Department heads in IT and security
- Chief Compliance Officer (CCO) and Chief Financial Officer (CFO)
All of these individuals have a stake in the process and will want to see an SRA lead to measures that bolster security posture. For the CFO, an SRA is part of a bigger responsibility of protecting all corporate assets from harm—a fiduciary duty realized through overall risk management and data security policies.
With the rise of cloud computing and Software as a Service (SaaS), security risk assessments are more crucial than ever. SaaS introduces new vulnerabilities by storing valuable data and operational processes on external platforms, increasing the risk of exposure. Additionally, SaaS applications can create third-party risks that businesses often have limited visibility into.
Benefits of Regular Security Risk Assessments
Even if you have to undergo a security risk assessment to comply with a specific standard like ISO 27001, the process brings many other security benefits, including:
- Improved Security Posture and Resilience—By identifying and prioritizing the most significant risks for mitigation, an SRA helps your enterprise better defend its most valuable digital assets, improving security posture and resilience.
- Better Incident Response Capabilities—Knowing which risks deserve the highest focus and investment helps your team be targeted and proactive in threat detection, risk management, and threat response.
- Lower Costs and Fewer Wasted Resources—An SRA highlights the highest priority risks, enabling you to avoid overspending on low-impact risks.
- Better Collaboration Across Departments—The SRA process fosters alignment and better collaboration among IT, security, business management, compliance, risk management, finance, and legal teams.
- Improved Third-Party Risk Management—An SRA helps stakeholders discover sources of third-party risk by evaluating partners and vendors.
How to Conduct a Security Risk Assessment in 5 Steps
A security risk assessment typically comprises five steps. The names of these steps may vary based on the framework or organizational context, but they answer the following five simple questions:
- What digital assets do we need to protect?
- What’s threatening them, and how are they vulnerable?
- What will happen if they are attacked and compromised?
- What should our priority be for managing risk for each identified asset?
- How will we keep this risk mitigation going over the long term?
Having a single person or small team executing the entire 5-step process is a good practice. They will be responsible for the following:
Step 1: Determine Scope
It’s essential to determine the scope of your SRA at the outset to answer this question so you can build the proper timelines and allocate the right resources. For instance:
- Will your security risk assessment analyze risks for the entire organization or a single business unit?
- Will it look at physical infrastructure, such as servers, data centers, software, data repositories, and networks?
- Will it examine third-party connections?
In some compliance scenarios, an SRA may only be required for a specific system, such as payment processing. Properly scoping the project is essential to ensure no risks are overlooked. The scoping process should begin with a stakeholder discussion and a whiteboard session to identify critical assets and resources. Then, complement this manual process with specialized tools that automate digital asset discovery. For example, in SaaS environments, Suridata can automatically inventory SaaS applications and map the data they contain—including those not officially sanctioned by IT (“Shadow SaaS”).
Step 2: Threat and Vulnerability Identification
With your asset inventory and scope of assessment, it’s time to determine what threats can cause risk exposure. For example, if you’re running an application server, you will discover hundreds of possible threats that could compromise it, like remote code execution (RCE) or SQL injection attacks. Threat intelligence sources like the MITRE ATT&CK knowledge base and the Cyber Threat Alliance can help with enriched threat information.
For organizations leveraging artificial intelligence in their operations, conducting an AI audit (a dedicated audit of AI systems and algorithms) can help identify unique vulnerabilities that may not be immediately evident through traditional assessments.
Some of the most serious threats in SaaS environments stem from third-party integrations. These plugins often allow one SaaS app to interact with another as a user, potentially granting access to sensitive data without oversight. An automated third-party integration monitoring tool like Suridata can detect and flag insecure plugins for remediation, helping to mitigate these hidden risks and implement SaaS security best practices.
Step 3: Risk Analysis
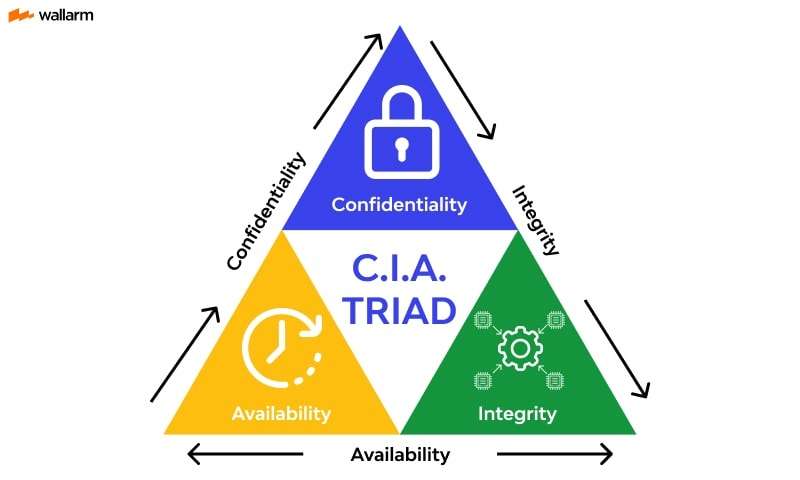
Just because a threat exists does not mean your digital assets will be exposed to risk. There are thousands of threats, and an equal, if not larger, number of vulnerabilities could cause problems. But will they? And, if a threat manifests in an attack, what will be its impact? This is where risk analysis comes into play. The risk analysis step of an SRA involves assessing the likelihood of a threat leading to a successful attack and the potential impact of such an event. The effect can be measured using the traditional information security “CIA Triad” (Confidentiality, Integrity, Availability) or by estimating the financial cost of a security incident. For instance, a breach that costs $100 to remediate has a much lower impact than one that costs $1 million.
Source
Suppose your e-commerce server is vulnerable to a cross-site scripting (XSS) attack that could allow a malicious actor to steal your customer list. How likely is the attack? What would the impact be? A common best practice is to rate probabilities on a scale from 1 to 5, with one meaning “rare” and five meaning “highly likely.” Similarly, impact can be rated from 1 (“minimal”) to 5 (“very severe”).
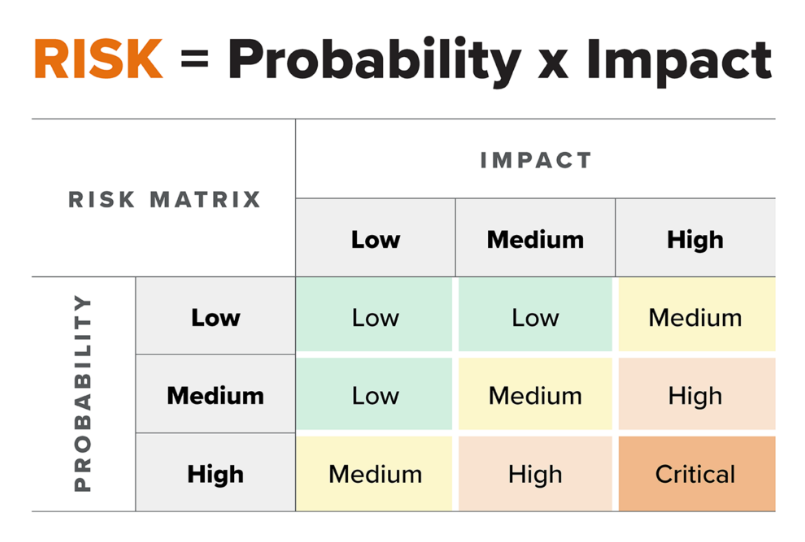
You can then plot your probabilities, impacts, and inferred risk level on a “Risk Matrix,” as shown here:
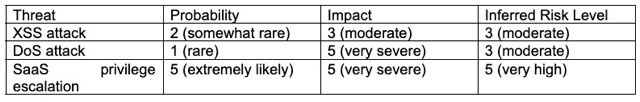
The Risk Matrix establishes the risk level for a given threat. In this example, even though a DoS attack has a very severe (level 5) impact, its probability is low (1). As a result, the overall risk level is moderate (3). Alternatively, a SaaS privilege escalation attack is highly likely (5) and very severe (5). The risk level is, therefore, very high (5).
If you’re modeling risk by cost, use Probability x Impact = Risk. With that approach, the risk matrix might look like this:
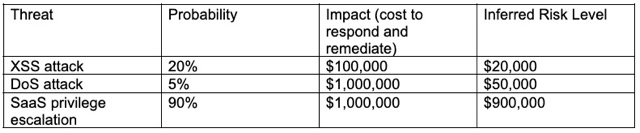
Step 4: Prioritization of Risks
The relative risk levels should generally translate into levels of prioritization for mitigation. Based on the matrix, SaaS privilege escalation should have the highest priority for a countermeasure. This is an imprecise process, though, and in some cases, you may want to take action even if the probability of an attack is low. For instance, if an outage in your e-commerce server will disrupt your business and brand, then DoS deserves high priority, no matter how unlikely it is to occur.
Prioritization of risks generally means taking one of three actions for a given risk:
- Avoid—Do not mitigate, but perhaps stop the process from occurring by, for example, removing an outdated server and replacing it with a more secure edition.
- Transfer—Transfer some or all of the risk to a third party, such as a cloud platform or a managed service provider (MSP). Cyber insurance can also serve this purpose.
- Mitigate—Take action to prevent the risk from occurring by patching systems or installing controls and countermeasures.
Dependency mapping is valuable to this process, revealing interdependent systems whose vulnerabilities might amplify overall risk.
After you’ve taken one of these steps, you’ll still have what’s known as “residual risk” – the remaining impact or costs that may persist even after implementing security controls. This is inevitable, and senior leadership must decide whether to implement further mitigations or accept the risk as an inherent part of business operations.
Step 5: Documentation and Monitoring of Risks
The final step involves documenting the work of the SRA team and recording it in a “Risk Register.” This document memorializes the risk, its applicable scenarios, when it was identified, risk level, and current mitigations. It forms the basis for ongoing monitoring and follow-ups. In most enterprises, an SRA is repeated periodically, once or twice a year. The Risk Register is essential for thorough and effective subsequent processes.
Getting An SRA Right
A five-step Security Risk Assessment (SRA) is optional for many companies. However, it’s a valuable process—even when not legally required. An SRA helps identify your most significant security risks, prioritize mitigation efforts, and save money and resources.
This five-step process begins by defining the scope and identifying critical assets. It is followed by threat and vulnerability identification, risk analysis, prioritization, and documentation. By the end, you’ll better understand where to focus your cybersecurity efforts.
With SaaS playing an increasingly prominent role in today’s risk landscape, security solutions must be designed to address its unique challenges. Suridata helps organizations assess SaaS risks during an SRA, identifying issues like insecure data storage, misconfigured SaaS applications, and third-party integration vulnerabilities.
To learn more, visit Suridata.ai or check out the Suridata demo.
Co-Founder & CPO
