How to Perform a Security Controls Assessment (SCA)
The rush to adopt new security paradigms often overshadows cybersecurity essentials. While we’re all jazzed about implementing a cool new software-as-a-service (SaaS) strategy, “doing” SASE or zero trust, we may overlook or lose sight of security controls, which are the foundation of security posture.
49% of CISOs worry they lack a clear picture of their organization’s vulnerabilities. This lack of visibility is especially true in complex SaaS environments, where it can be challenging to verify control effectiveness.
Controls only count if they work, and regular SCAs are crucial to ensuring they do. A Security Controls Assessment (SCA) helps by testing and confirming that they are working as intended.
What is a Security Controls Assessment (SCA)?
In cybersecurity, a security control typically combines policy, process, and technology to realize a control objective. For instance, if the aim is to prevent non-employees from accessing a SaaS application, an effective control could enforce a policy that requires SaaS users to have a valid employee ID number. This objective is then connected to a control activity, which might involve an automated check to verify each user’s ID against an employee database before granting access.
A Security Controls Assessment (SCA) evaluates whether security controls work as intended to meet specific objectives. For example, if you aim to ensure that “vulnerabilities in assets are identified, validated, and recorded” (per the NIST CSF Risk Assessment RA-01), you might rely on a vulnerability management tool as a control activity to identify unpatched software.
Conducting an SCA for this control would reveal whether these tools effectively identify vulnerabilities, such as unpatched software, as intended. SCA is particularly relevant for SaaS, where misconfigurations in SaaS apps can cause significant risk exposure.
Why Do You Need a Security Controls Assessment (SCA)?
There are other ways of assessing controls, such as “red teaming” and penetration testing. These methods are effective but tend to be comparatively costly and intermittent. Controls, however, may change over time, and a periodic red teaming exercise could leave a problem undetected for months. This issue can be particularly acute in a SaaS environment, where SaaS providers frequently update their code, and changes may cause security settings to shift without being detected.
An SCA offers a more thorough, proactive, and consistent approach to testing controls. SCAs can cover any control type and work across the significant domains of cybersecurity, including:
- Application security– evaluating API security practices or assessing how well code scanning controls detect malware in open-source software libraries.
- Data security– verifying data encryption protocols.
- Identity and access management (IAM)– assessing access controls.
- Incident response– examining and testing incident response plans and workflows.
- SaaS security– determining whether SaaS solutions can detect unauthorized “shadow SaaS” instances.
- Infrastructure security– detecting configuration flaws or inspecting patch management processes.
SCAs also support regulatory compliance. Regulations like HIPAA, which mandates access controls for health records, or SOX, which requires separation of duties, rely on adequate security controls. For example, the U.S. Center for Medicare and Medicaid Services requires businesses it interacts with to perform SCAs as part of its “Acceptable Risk Safeguards” policy.
How to Perform a Security Controls Assessment (SCA)
How you perform an SCA will depend on the size and nature of your organization, but here are some common steps that should apply to all:
1. Define the SCA’s Scope and Objectives
Select a group of controls you can assess thoroughly and accurately. One way to determine the target controls for the SCA is to work from an existing control framework, such as NIST CSF, ISO 27002, or CIS Critical Security Controls. You can also base your choices on compliance, such as selecting the SOX IT General Controls (ITGCs) or application controls (ITACs).
Another proven approach is to start by inventorying your most valuable information assets. Which systems are critical for your business? What data is the most important to defend? Some of these may be located in the cloud, on SaaS apps, or in places you know nothing about until you do an automated data discovery scan. With that inventory, you can look for the controls that protect those assets.
Some refer to this as the control’s “heatmap.” It guides you to the controls that matter most to your security posture and overall risk management goals.
2. Determine the Organizational Aspects of the SCA
An SCA doesn’t operate in isolation; it requires clear ownership and defined responsibilities. In larger organizations, a full-time role may be dedicated to SCA, but more often, it’s a shared responsibility among individuals with other duties.
Successful SCA implementation may involve several “dotted line” relationships among teams and individuals contributing to the process. To avoid confusion, everyone involved should clearly understand their roles, and any contractors or consultants should be aware of project expectations. Managers play a crucial role by ensuring team members have the flexibility in their schedules to prioritize SCA-related tasks effectively.
3. Select Your SCA Tooling
You can find SCA solutions that handle many of the control assessments you need to make. These tools simulate attacks, often using the latest threat intelligence and a high degree of automation. They may also combine static testing (SAST) and dynamic testing (DAST) to cover a breadth of controls and threats. However, testing SaaS controls requires a specialized SaaS security solution like Suridata, which can continuously monitor controls affecting SaaS configuration and shadow SaaS.
4. Gather Information on Controls
This step may occur earlier in the process, but collecting information on each control you want to assess (including its objective and activity) is crucial. Some of this may already exist in control documentation, but you’d be surprised how bare that cupboard can be sometimes. It’s up to you to ensure you’re testing the control against its objective. Otherwise, how would you know if it’s working right?
5. Test the Controls and Perform Vulnerability Assessment
Now comes the actual testing and assessment. This process may require evaluating the vulnerabilities and threats affecting the control’s effectiveness. The SCA solution and other technologies employed for the SCA generate significant amounts of data in this stage. If your SCA involves SaaS, you may require a separate platform for SaaS security, feeding into the SCA dataset. You have to analyze that data or configure the SCA solution to demonstrate how well or deficiently the control functions.
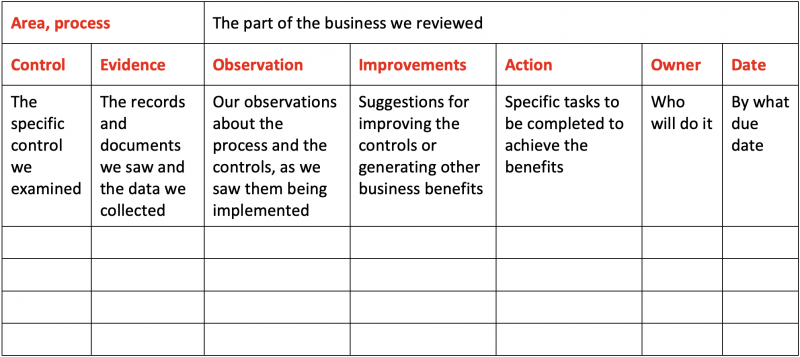
6. Controls Documentation Review and Updating
With SCA data, you must report your findings and explain which controls were adequate or deficient. It is crucial to update controls’ documentation as part of this process. For example, you may discover that an existing control activity relies on an integration that is no longer supported. It should be replaced by one that will enable the control activity.
7. Remediate Issues
The SCA process typically involves either remediating deficient controls directly or assigning those tasks to a dedicated team. Ideally, the SCA solution can automate remediation tasks; for instance, Suridata automates the shutdown of insecure third-party SaaS integration plugins.
You should also assess incident response capabilities where relevant. For example, suppose a data security control mandates removing sensitive data from SaaS applications. In that case, the SCA should verify that this removal happens quickly, reliably, and in a fully auditable way.
The SCA process is never truly “finished.” The critical question is how frequently you will repeat the assessment. Sometimes, an SCA tool may run continuously, ensuring constant oversight. Regardless of how often you perform SCA, continuous improvement should be a guiding principle, with each evaluation followed by discussions on enhancing control effectiveness and refining the SCA process.
Getting Ready to Hit “Go” on SCA
SCAs may seem overwhelmingly complex if you’ve never done one before. These assessments do take effort, but the good news is that once you’ve done your first SCA, the next time gets much easier. Success relies on identifying your most important controls and finding the proper SCA tooling, so the process is as automated as possible.
For new control areas, like the cloud and SaaS, the answer may come from purpose-built SaaS security solutions like Suridata. These solutions can help you automate many of the SCA steps and provide clear guidance and information on the state of your SaaS controls. Learn more here.
Co-Founder & CPO
