The New York Times GitHub Breach: What You Need to Know
Recently, the security landscape has been shaken by several high-profile breaches, and the latest incident involving GitHub tokens has once again highlighted the critical importance of Machine-to-Machine security practices. This blog dives deep into the details of The New York Times GitHub token breach that exposed the entire source code of The New York Times, its implications, and what organizations can do to safeguard their systems.
A Bad Time for The New York Times: Entire Source Code Exposed
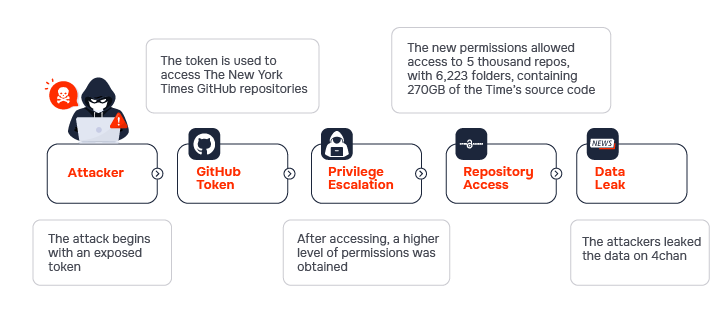
Using a stolen GitHub token, attackers exploited access to The New York Times’ GitHub repositories.
This token was overprivileged, granting access to all repositories within The New York Times GitHub organization. It is probable that the token was poorly managed, having a long expiry period, being leaked through accidental public exposure, stored on a compromised employee’s device, or used by an ex-employee to access private GitHub content.
This breach underscores the risks associated with SaaS application tokens, which are often the most vulnerable points and the entry point to the organization’s sensitive data.
What Happened?
The breach occurred in January 2024 when attackers used a stolen GitHub token to access The New York Times’ repositories. The attacker leaked data, which included 270GB and over 5,000 repositories, with fewer than 30 being encrypted. The stolen files contained IT documentation, infrastructure tools, and source code, including the viral Wordle game.
The Impact
The impact of this breach is far-reaching:
- Repository Access: Attackers could access private repositories, leading to data leaks and exposure of proprietary code.
- Data Manipulation: With write access, malicious actors could alter or delete critical code, inject malicious code, or disrupt development processes.
How Could Suridata Help?
At first, to prevent such breaches, Suridata protects your repositories and data at GitHub, with the following best practices:
- Token Management: Suridata maintains an inventory of your GitHub tokens, allowing investigation for each one. This includes the latest access, and expiration dates.
- Regular Token Rotation: Suridata alerts you to rotate tokens frequently to minimize the impact of potential breaches.
- Implement Least Privilege: Suridata displays the permissions granted to tokens and recommends the minimum necessary for their operation.
- Breach Detection: Suridata continuously monitors all tokens across the SaaS environments, detecting anomalies in usage and changes in roles and permissions.
Following a potential breach, Suridata responds as follows:
- Revoking Tokens: Revoking any compromised tokens to prevent further unauthorized access.
- User Notification: Promptly notify impacted users, advising them to regenerate their tokens and review repository access logs.
Conclusion
Organizations must remain proactive in securing their development environments, especially when they are easily accessed through tokens. By continuously improving defenses, and embracing automated responses, organizations can better protect their valuable assets from evolving threats.
Not sure if you are using GitHub? Suridata offers free application scanning to help you identify and prevent attacks in your SaaS environments.
Product Lead
